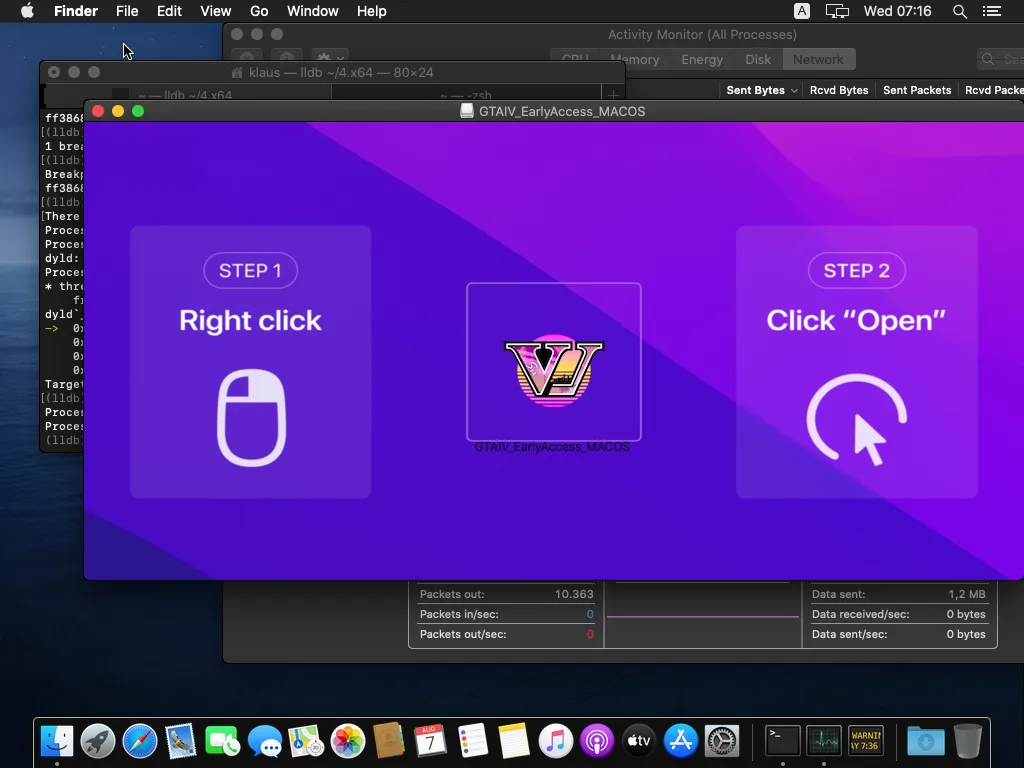
Cado Safety’s discovery has completely debunked the assumption that macOS methods are impervious to malware. This revelation considerations a brand new malware-as-a-service (MaaS) referred to as “Cthulhu Stealer,” which targets macOS customers by means of misleading means.
The rise of Cthulhu Stealer signifies that no system is totally safe in opposition to cyber threats.
How Malware Steals Mac Customers’ Crypto?
Cthulhu Stealer disguises itself as respectable purposes comparable to CleanMyMac and Adobe GenP and software program claiming to be an early launch of “Grand Theft Auto VI.”
As soon as the consumer mounts the malicious DMG file, they’re prompted to enter the system and MetaMask passwords. This preliminary deception is only the start.
Learn extra: A Information to the Greatest AI Safety Options in 2024
Following the credentials enter, the malware makes use of osascript, a macOS software, to extract passwords from the system’s Keychain. This information, together with particulars from crypto wallets like MetaMask, Coinbase, and Binance, is compiled into a zipper archive. This archive, recognized by the consumer’s nation code and the time of the assault, comprises the stolen info.
Cthulhu Stealer additionally steals information from different platforms, together with:
- Chrome extension wallets
- Minecraft consumer info
- Wasabi pockets
- Keychain passwords
- SafeStorage passwords
- Battlenet recreation, cache, and log information
- Firefox cookies
- Daedalus pockets
- Electrum pockets
- Atomic pockets
- Concord pockets
- Electrum pockets
- Enjin pockets
- Hoo pockets
- Dapper pockets
- Coinomi pockets
- Belief pockets
- Blockchain pockets
- XDeFi pockets
- Browser cookies
- Telegram Tdata account info
Furthermore, Cthulhu Stealer collects detailed system info comparable to IP deal with, system title, and OS model. It then sends this information to a command and management (C2) server, enabling the attackers to refine their methods.
Scammers Cost $500/Month For Cthulhu Stealer
Scammers use varied methods to entice the victims into putting in the malware. For instance, on social media, some scammers pose as employers who supply jobs that require downloading software program to trace working hours. These provides include a way of urgency, pushing the potential sufferer to obtain the applying rapidly.
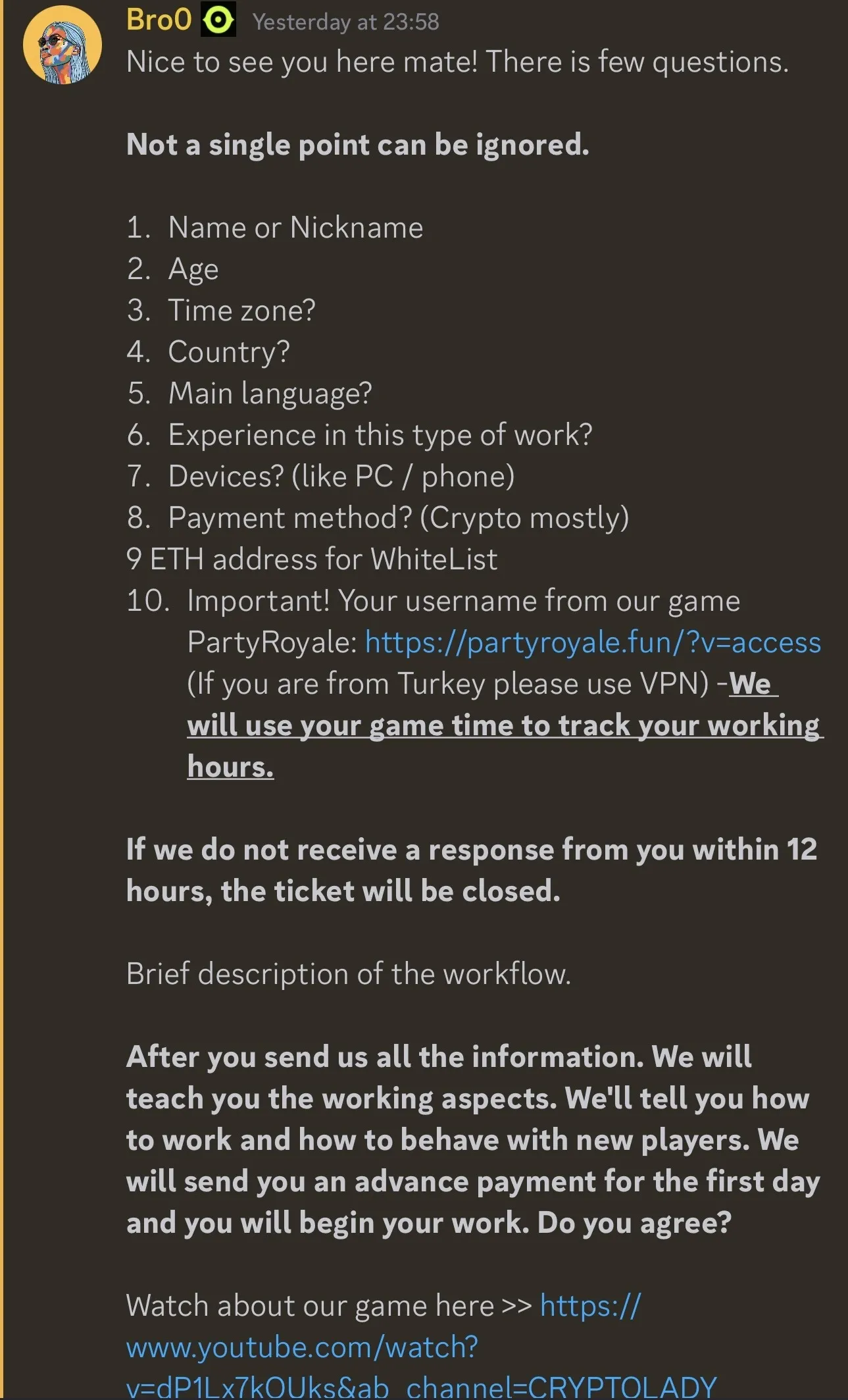
The builders and associates behind Cthulhu Stealer, generally known as the Cthulhu Group, use Telegram to handle their operations.
“The stealer appears to be being rented out to individuals for $500/month, with the main developer paying out a percentage of earnings to affiliates based on their deployment. Each affiliate of the stealer is responsible for the deployment of the malware. Cado has found Cthulhu stealer sold on two well-known malware marketplaces which are used for communication, arbitration and advertising of the stealer, along with Telegram,” Cado knowledgeable readers.
Learn extra: 9 Crypto Pockets Safety Suggestions To Safeguard Your Property
To guard themselves, customers ought to set up respected antivirus software program that’s particularly designed for macOS. They need to even be cautious of employment alternatives that require instant software program downloads. Common software program updates can additional scale back the danger of malware infections.
Disclaimer
In adherence to the Belief Undertaking tips, BeInCrypto is dedicated to unbiased, clear reporting. This information article goals to offer correct, well timed info. Nonetheless, readers are suggested to confirm details independently and seek the advice of with an expert earlier than making any choices based mostly on this content material. Please observe that our Phrases and Circumstances, Privateness Coverage, and Disclaimers have been up to date.